- +1-315-215-1633
- sales@thebrainyinsights.com

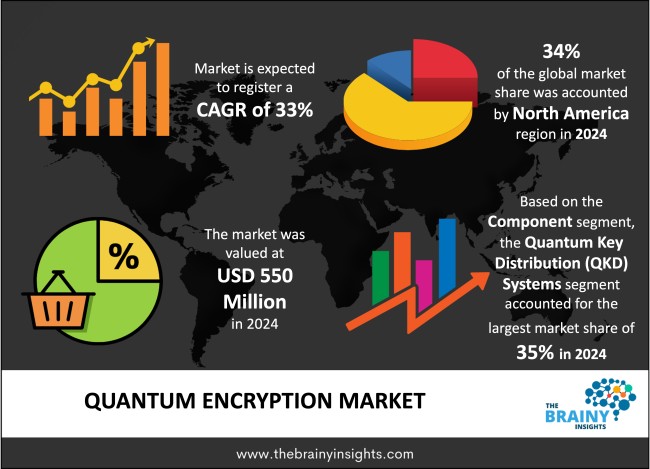
The global quantum encryption market was valued at USD 550 million in 2024 and grew at a CAGR of 33% from 2025 to 2034. The market is expected to reach USD 9,525.31 million by 2034. The rising applications of quantum computing will drive the growth of the global quantum encryption market.
Quantum encryption makes use of the basic ideas of quantum mechanics to make communication much safer than current methods. Essentially, quantum encryption depends on Quantum Key Distribution (QKD). With QKD, two parties are able to make and exchange a cryptographic key across a quantum channel. Quantum superposition and the no-cloning theorem make sure that the process is secure, as stated by quantum physics laws. When a third party tries to get the key using a quantum system, the key will be affected and the intrusion would be instantly noticed. Two communication parties use quantum bits (qubits), sent using photons’ polarization or phase, in QKD. Among QKD protocols, BB84 and E91 are the leading examples, made to stop hackers from reading any shared keys. When the key is safe, it is possible to use conventional encryption like the one-time pad for encrypting messages with total privacy. More and more attention is being given to quantum encryption because the rise of quantum computers may break most of today’s classical encryption schemes. The ability of quantum computers to compute certain problems very quickly makes today’s cryptography code easily breakable. The technology has come up with a new kind of security that depends on nature and not on computing, so quantum encryption can withstand all future risks.
Get an overview of this study by requesting a free sample
New developments in quantum computing – Businesses can use quantum encryption more easily and confidently because of new developments in quantum computing and communication which encourages them to adopt it. The increasing number of cyberattacks and data breaches have encouraged companies to use quantum encryption for better protection of their data. By investing a lot in research and development, both private organizations and government groups have quickly brought quantum encryption technologies to a point where they are useful and accessible outside of research. Since finance, defence, healthcare, and government sectors deal with secret information, they are motivated to use quantum-safe encryption methods. Besides, the increasing ability to integrate quantum encryption with standard cryptography systems lowers the main barriers to its implementation inside companies. All in all, the main motivations for adopting quantum encryption are technological growth, stronger security awareness, dedicated R&D work, unique needs for data protection in different sectors, compatibility with present systems, and cost benefits.
Technological, financial and personnel problems – Challenges that limit the use of quantum encryption are mostly due to problems with technology, finances, and personnel. High costs are still a big obstacle when it comes to using quantum encryption. Research, setting up, and carefully maintaining the equipment and special software are all expensive, and this can restrict small and medium businesses from using them. Quantum encryption is complex, and few businesses are willing to adopt it because it has not been demonstrated in big or complex settings. It is difficult to merge quantum encryption systems into existing IT networks and legacy security protocols, since this usually requires the organization to make major changes and have qualified engineers. It is difficult to overcome this challenge because there are few experts who know about both quantum technologies and cybersecurity. Since it’s challenging for organizations to manage these systems due to the lack of experts, many are not motivated to start using them. On top of this, organizations not in sensitive fields usually believe their current protection is enough against existing dangers. The combination of high expenses, technology’s complexity, lack of skilled personnel, integration limits, and the priorities of various industries result in many organizations not adopting and implementing quantum encryption.
The increasing incidence of cyberattacks – The constant rise in advanced cyberattacks and threat of quantum computers breaking existing ways of encryption forces companies and governments to apply quantum encryption to ensure their security. Governments across the world are increasing their cybersecurity rules, which forces organizations to put in place advanced technology such as quantum encryption. People are now much more interested in keeping their data safe, so companies are working to prove they care about people’s privacy by improving their security systems. More and more devices and platforms are joining the online world, which makes securely transferring data even more important, leading to the increased demand for quantum-safe encryption. Also, the increase in geopolitical issues and the threat of data theft from espionage around the world ensure that unbreakable encryption methods are needed even more urgently. As a result of all these forces, companies and industries are encouraged to introduce quantum encryption to ensure their data is safe from new threats.
The regions analyzed for the market include North America, Europe, South America, Asia Pacific, the Middle East, and Africa. North America emerged as the most significant global quantum encryption market, with a 34% market revenue share in 2024.
Many important companies, research institutes, and governmental organizations in the region work to advance and improve the accessibility of quantum encryption. Quantum technology has become so important in the U.S. that it has become a national priority, and large amounts of money are being spent through the National Quantum Initiative Act to fast-track the research, building, and commercialization of these systems. North America has big companies, growing startups, and research centres in these two fields which augments the market’s growth. Furthermore, both businesses and government organizations in this area are working actively to put in place advanced security technologies to safeguard important data from the evolving nature of cyberattacks. Also, the advanced telecommunications system across North America makes it easy to set up quantum encryption systems for experiments and trials.
North America Region Quantum Encryption Market Share in 2024 - 34%
www.thebrainyinsights.com
Check the geographical analysis of this market by requesting a free sample
The component segment is divided into quantum key distribution (QKD) systems, quantum random number generators (QRNG), quantum cryptographic protocols and software & services. The quantum key distribution (QKD) systems segment dominated the market, with a market share of around 35% in 2024. The majority of the world’s quantum encryption market is led by Quantum Key Distribution (QKD) due to its basic role in providing trustworthy and exclusive key exchange. Unlike earlier ways of sharing keys that depend on complicated algorithms, QKD is based on quantum mechanics and ensures security by using the ideas of the no-cloning theorem and behaviour of quantum particles. Added to that, QKD is gaining popularity because it is now technically advanced and widely available in the market. In the last decade, improvements in photon sources, detectors, and quantum communication protocols have increased how far and how reliably QKD systems can be used in today’s telecom systems. The first places QKD is used most are in governments, agencies, and businesses, thanks to their vital need for strong data security. In addition, many projects are currently deploying quantum networks to boost security for communication locally and all over the nation, which helps improve QKD’s dominant place. One more reason for QKD’s dominance is that it is the main technology behind several quantum encryption methods.
The application segment is divided government & defence, banking & financial services, healthcare, telecommunications, IT & data centres and energy & utilities. The government and defence segment dominated the market, with a market share of around 37% in 2024. Since governments and military groups handle a lot of classified details, they are very likely to benefit from quantum encryption and choose services like Quantum Key Distribution (QKD). Due to its ability to break regular cryptography, quantum computers represent a major danger to national protection, making these bodies speed up the development of quantum-safe encryption software. Besides, it is common for government bodies and dedicated agencies to take the lead in developing and applying quantum encryption because they have the funds and strategies to keep their systems advanced and secure. Regulations and policies have been set in both defence and government industries, requiring use of advanced encryption to secure important data, and this increases the demand for such services. In addition, governments work together with universities and technology companies to invent top-notch quantum encryption technologies, which plays a role in encouraging innovation and building a strong market.
The deployment type segment is divided into on-premises and cloud-based. The on-premises segment dominated the market, with a market share of around 58% in 2024. Control, security, and customizing capabilities are major reasons why the on-premises deployment segment leads the world’s quantum encryption market. Essentially, on-premises environments require installing and managing quantum encryption systems on the organization’s network, which greatly aids in controlling and connecting them to other IT systems. Using quantum encryption on company servers allows organizations to adjust the solutions for their own security needs, something that usually is not possible with cloud deployments. As a result, firms are equipped to work more efficiently, deal with risks in a better way, and meet all the necessary rules within their organization and those set by outside authorities. Also, many companies still hesitate to move their most valuable encryption keys and sensitive data to the cloud because of the possibility of weaknesses on the part of third parties and their questions about who owns the data. As currently, quantum communication networks are limited to specialized channels and tools that most companies don’t have access to, it is more useful to deploy such systems locally.
The end-user segment is divided large enterprises and small and medium enterprises (SMEs). The large enterprises segment dominated the market, with a share of around 67% in 2024. Many organizations cover all kinds of sensitive data in industries like finance, healthcare, telecommunications, and government payments, so the use of advanced encryption makes cyber security much safer for them. Many large enterprises have what it takes to pay for the high prices of quantum encryption systems, as well as purchase new hardware, update their networks, and train workers. The use of skilled people and special teams in cybersecurity helps businesses manage and combine quantum encryption with their current security setup. Also, because big companies must obey strict rules in data protection, they are driven to choose better encryption. Since they are usually first to adopt new technologies, big companies team up with technology firms and research institutes to guide changes in the market. Overall, these points secure their dominance in quantum encryption since they are at the forefront of moving toward safer data protection in the future.
| Attribute | Description |
|---|---|
| Market Size | Revenue (USD Million) |
| Market size value in 2024 | USD 550 Million |
| Market size value in 2034 | USD 9,525.31 Million |
| CAGR (2025 to 2034) | 33% |
| Historical data | 2021-2023 |
| Base Year | 2024 |
| Forecast | 2025-2034 |
| Region | The regions analyzed for the market are Asia Pacific, Europe, South America, North America, and Middle East and Africa. Furthermore, the regions are further analyzed at the country level. |
| Segments | Component, Application, Deployment Type and End-User |
As per The Brainy Insights, the size of the global quantum encryption market was valued at USD 550 million in 2024 to USD 9525.31 million by 2034.
Global quantum encryption market is growing at a CAGR of 33% during the forecast period 2025-2034.
The market's growth will be influenced by new developments in quantum computing.
Technological, financial and personnel problems could hamper the market growth.
This study forecasts revenue at global, regional, and country levels from 2021 to 2034. The Brainy Insights has segmented the global quantum encryption market based on below mentioned segments:
Global Quantum Encryption Market by Component:
Global Quantum Encryption Market by Application:
Global Quantum Encryption Market by Deployment Type:
Global Quantum Encryption Market by End-User:
Global Quantum Encryption Market by Region:
Research has its special purpose to undertake marketing efficiently. In this competitive scenario, businesses need information across all industry verticals; the information about customer wants, market demand, competition, industry trends, distribution channels etc. This information needs to be updated regularly because businesses operate in a dynamic environment. Our organization, The Brainy Insights incorporates scientific and systematic research procedures in order to get proper market insights and industry analysis for overall business success. The analysis consists of studying the market from a miniscule level wherein we implement statistical tools which helps us in examining the data with accuracy and precision.
Our research reports feature both; quantitative and qualitative aspects for any market. Qualitative information for any market research process are fundamental because they reveal the customer needs and wants, usage and consumption for any product/service related to a specific industry. This in turn aids the marketers/investors in knowing certain perceptions of the customers. Qualitative research can enlighten about the different product concepts and designs along with unique service offering that in turn, helps define marketing problems and generate opportunities. On the other hand, quantitative research engages with the data collection process through interviews, e-mail interactions, surveys and pilot studies. Quantitative aspects for the market research are useful to validate the hypotheses generated during qualitative research method, explore empirical patterns in the data with the help of statistical tools, and finally make the market estimations.
The Brainy Insights offers comprehensive research and analysis, based on a wide assortment of factual insights gained through interviews with CXOs and global experts and secondary data from reliable sources. Our analysts and industry specialist assume vital roles in building up statistical tools and analysis models, which are used to analyse the data and arrive at accurate insights with exceedingly informative research discoveries. The data provided by our organization have proven precious to a diverse range of companies, facilitating them to address issues such as determining which products/services are the most appealing, whether or not customers use the product in the manner anticipated, the purchasing intentions of the market and many others.
Our research methodology encompasses an idyllic combination of primary and secondary initiatives. Key phases involved in this process are listed below:
The phase involves the gathering and collecting of market data and its related information with the help of different sources & research procedures.
The data procurement stage involves in data gathering and collecting through various data sources.
This stage involves in extensive research. These data sources includes:
Purchased Database: Purchased databases play a crucial role in estimating the market sizes irrespective of the domain. Our purchased database includes:
Primary Research: The Brainy Insights interacts with leading companies and experts of the concerned domain to develop the analyst team’s market understanding and expertise. It improves and substantiates every single data presented in the market reports. Primary research mainly involves in telephonic interviews, E-mail interactions and face-to-face interviews with the raw material providers, manufacturers/producers, distributors, & independent consultants. The interviews that we conduct provides valuable data on market size and industry growth trends prevailing in the market. Our organization also conducts surveys with the various industry experts in order to gain overall insights of the industry/market. For instance, in healthcare industry we conduct surveys with the pharmacists, doctors, surgeons and nurses in order to gain insights and key information of a medical product/device/equipment which the customers are going to usage. Surveys are conducted in the form of questionnaire designed by our own analyst team. Surveys plays an important role in primary research because surveys helps us to identify the key target audiences of the market. Additionally, surveys helps to identify the key target audience engaged with the market. Our survey team conducts the survey by targeting the key audience, thus gaining insights from them. Based on the perspectives of the customers, this information is utilized to formulate market strategies. Moreover, market surveys helps us to understand the current competitive situation of the industry. To be precise, our survey process typically involve with the 360 analysis of the market. This analytical process begins by identifying the prospective customers for a product or service related to the market/industry to obtain data on how a product/service could fit into customers’ lives.

Secondary Research: The secondary data sources includes information published by the on-profit organizations such as World bank, WHO, company fillings, investor presentations, annual reports, national government documents, statistical databases, blogs, articles, white papers and others. From the annual report, we analyse a company’s revenue to understand the key segment and market share of that organization in a particular region. We analyse the company websites and adopt the product mapping technique which is important for deriving the segment revenue. In the product mapping method, we select and categorize the products offered by the companies catering to domain specific market, deduce the product revenue for each of the companies so as to get overall estimation of the market size. We also source data and analyses trends based on information received from supply side and demand side intermediaries in the value chain. The supply side denotes the data gathered from supplier, distributor, wholesaler and the demand side illustrates the data gathered from the end customers for respective market domain.
The supply side for a domain specific market is analysed by:
The demand side for the market is estimated through:
In-house Library: Apart from these third-party sources, we have our in-house library of qualitative and quantitative information. Our in-house database includes market data for various industry and domains. These data are updated on regular basis as per the changing market scenario. Our library includes, historic databases, internal audit reports and archives.
Sometimes there are instances where there is no metadata or raw data available for any domain specific market. For those cases, we use our expertise to forecast and estimate the market size in order to generate comprehensive data sets. Our analyst team adopt a robust research technique in order to produce the estimates:
Data Synthesis: This stage involves the analysis & mapping of all the information obtained from the previous step. It also involves in scrutinizing the data for any discrepancy observed while data gathering related to the market. The data is collected with consideration to the heterogeneity of sources. Robust scientific techniques are in place for synthesizing disparate data sets and provide the essential contextual information that can orient market strategies. The Brainy Insights has extensive experience in data synthesis where the data passes through various stages:
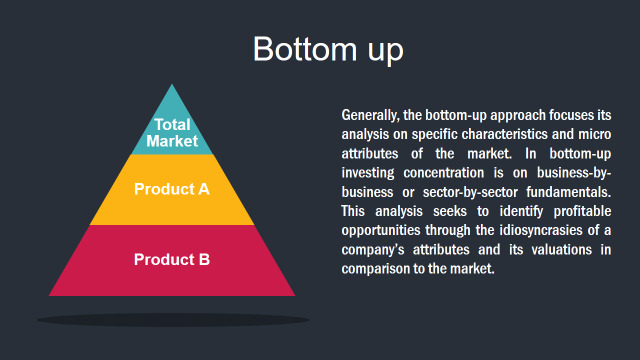
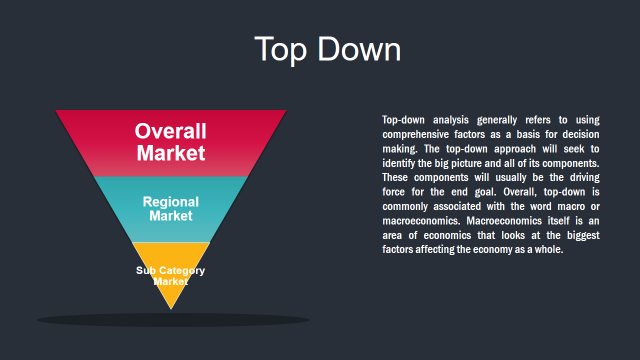
Market Deduction & Formulation: The final stage comprises of assigning data points at appropriate market spaces so as to deduce feasible conclusions. Analyst perspective & subject matter expert based holistic form of market sizing coupled with industry analysis also plays a crucial role in this stage.
This stage involves in finalization of the market size and numbers that we have collected from data integration step. With data interpolation, it is made sure that there is no gap in the market data. Successful trend analysis is done by our analysts using extrapolation techniques, which provide the best possible forecasts for the market.
Data Validation & Market Feedback: Validation is the most important step in the process. Validation & re-validation via an intricately designed process helps us finalize data-points to be used for final calculations.
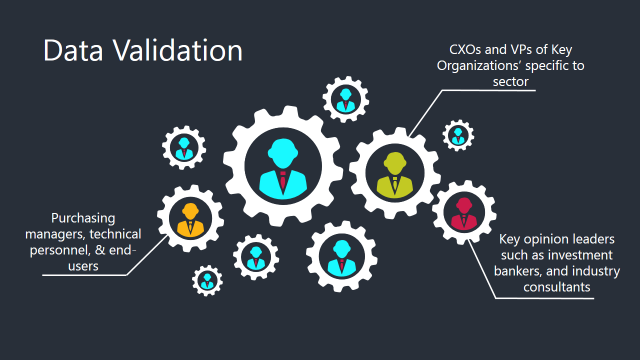
The Brainy Insights interacts with leading companies and experts of the concerned domain to develop the analyst team’s market understanding and expertise. It improves and substantiates every single data presented in the market reports. The data validation interview and discussion panels are typically composed of the most experienced industry members. The participants include, however, are not limited to:
Moreover, we always validate our data and findings through primary respondents from all the major regions we are working on.
Free Customization
Fortune 500 Clients
Free Yearly Update On Purchase Of Multi/Corporate License
Companies Served Till Date